nebman nebula manager
I started using Nebula as my personal mesh/ vpn choice some time ago, I only have a few static machines in the mesh but one thing I wanted to do was to add any lab machines to the same mesh so I could access them all the time. This tended not to happen as I would spin a machine up for a week or so so I wouldn't go to the bother of creating certs, pushing them and setting up the service. nebman (Nebula Manager) is my attempt to simplify the process and ensure I can add all lab machines quickly.
The README on the nebman Github page lists some big caveats, primarily in it's current state it is fit for the purpose I have but I intend to develop it further to make it more robust and fit more use cases. This page is a walkthrough/ guide for using nebman in it's current state.
office365 mfp smtp config high volume email
I've configured multiple MFPs in the past, for email sending of attachments. With Exchange Online this became a little more complicated but app passwords did the trick, I recently came across a doc indicating that all basic authentication would be disabled next year so took a look at the suggested alternative.
jupyter python venv
A very short note on a recent Python package setup on Windows. Requirement was to install Jupyter and some require packages for the script without conflicting with existing software on the machine and to allow easy access to run it.
setup nebula mesh
I've been using Wireguard for years to access some key servers from wherever I am without even thinking about it, recently I've been testing a few new services and decided to try another method for getting access to them, one that would not require any action on existing enabled devices. I remember trying nebula some years back, I think I didn't bother making it permentant as Wireguard was working fine for me at the time.
To set this up the plan is to:
- Setup
nebula-certlocally for genertation of certs. - Manually setup 1 x standard node.
- Manually setup 1 x lighthouse node (lighthouse is a publically accessible server, at least one is required for best results).
- Automate the process to add additional standard nodes using python or ansible or a combination of both.
zabbix server installation
I have a very neglected Nagios installation on my LAN monitoring some servers/ services. I never got around to adding additional items to monitor. Finally getting around to it now, I decided to setup a Zabbix server instead as I've used it more recently in production and I know it's pretty straight forward to add additional items to be monitored. The hope being I will be more inclined to keep it up to date.
Install is taken from the excellent documentation, listing my specific steps to help if I ever have to re-do. I'm installing Zabbix 6.4 on a minimal install of Ubuntu Server 22.04.2 LTS.
increase virtual disk with lvm
After moving to a new VM platform I had a large amount of data to transfer from the old host to a new disk on a VM. In order to work within the availalbe space I had to transfer a lot of data, delete it from the host and then grow the disk on the VM so I could transfer the rest of the data over.
First step was to add the initial disk to the VM and bring it online and get it mounted.
azure sentinel setup
For whatever reason, most of the content and training I've consumed to gain better understanding into cyber security has been focused on open source technologies. Someone recently suggested I take a look at Microsoft Sentinel, I looked through some Microsoft Learn content and while the content is very good and informative, I much prefer to learn by doing so decided to implement a quick trial.
Most of the content and steps will be taken from content direct from Microsoft but my goal is, should the opportunity arise for a production implementation in the future, I'll have a jump on things.
azure backup restore protected files
Restoring select files and folders from Azure backup is a straight forward process, a disk is mounted in the OS you're restoring to and you can just browse and copy/ paste what you want out. There can be permissions issues however that add some complications to this. Two examples that spring to mind are:
- You have a folder with very restricted access (think management or CEO) and by design Domain Admins do not have access.
- You've setup redirected folders using Microsoft's recommended configuration which by design, has restrictive permissions.
There should be no issue with the above, the backup runs under System so the files get backed up however the way Azure backup does selective files/ folder restores adds complications. The mount is read only (so you can't change ownership) and the permissions persist in the mount (so your admin ac won't have access).
signing-powershell-scripts
Unauthorised PowerShell scripts can and should be a cause of concern on a network, at the higher end of the risk level many Windows malware or Ransomware campaigns can utilise PowerShell scripts as part of their attack. Blocking PowerShell scripts entirely is not an ideal solution so setting a secure policy Domain wide is a good middle ground.
Key steps for the process are:
- Set domain wide policy.
- Create a code signing certificate and distribute.
- Sign our PowerShell script.
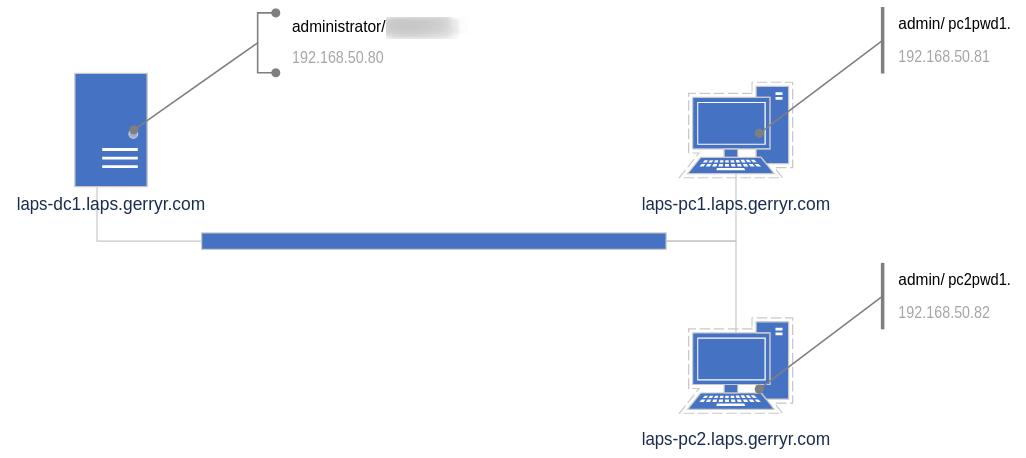
microsoft laps setup
I never got around to deploying Microsoft Local Administrator Password Solution (LAPS) in the previous domains I managed but it seems more and more like a tool I would want to deploy to help reduce lateral movement or domain wide exposure in an Ransomware situation. I'm going through the setup and config in a test environment to see what's what.